Path Traversal Reprise Licence Manager (CVE-2018-5716)
This post will demonstrate a vulnerability in the Reprise Licence Manager (RLM) version 11.0 found while doing a pentest. The vulnerability in question allows a user with access to the Web Management Interface to access (and sometimes write) files in the System.
This vulnerability allows to access files, and therefore gather additional info about the system, and also delete the log file of the RLM server (in case of the file write permission).
This situation was reported to the Reprise Software Inc. and was promptly considered NOT A VULNERABILITY since the application was to be installed as a non-privileged user. However I strongly disagree since an attacker can access some files that are available for all users on the system. This issue could be easily resolved by having a list of files where the application can access and limit the access to the Web Application only.
A CVE (CVE-2018-5716) was issued for this vulnerability and is going to be released soon.
Without any further ado here comes the details of it:
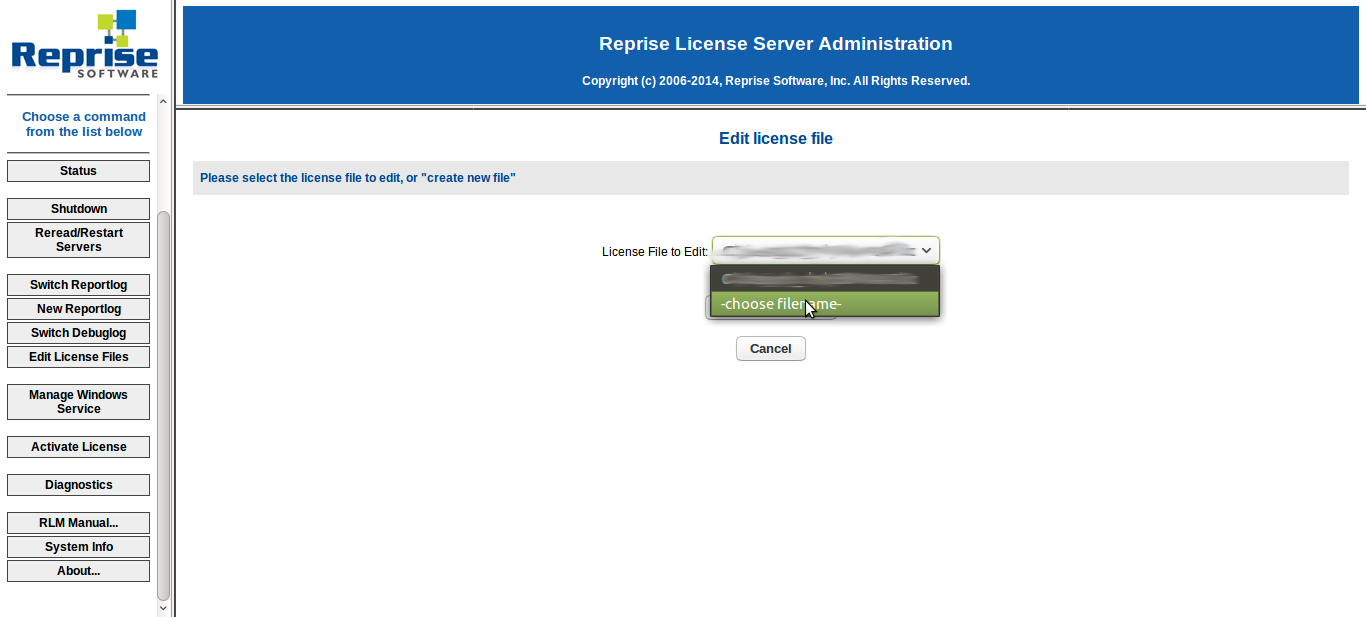
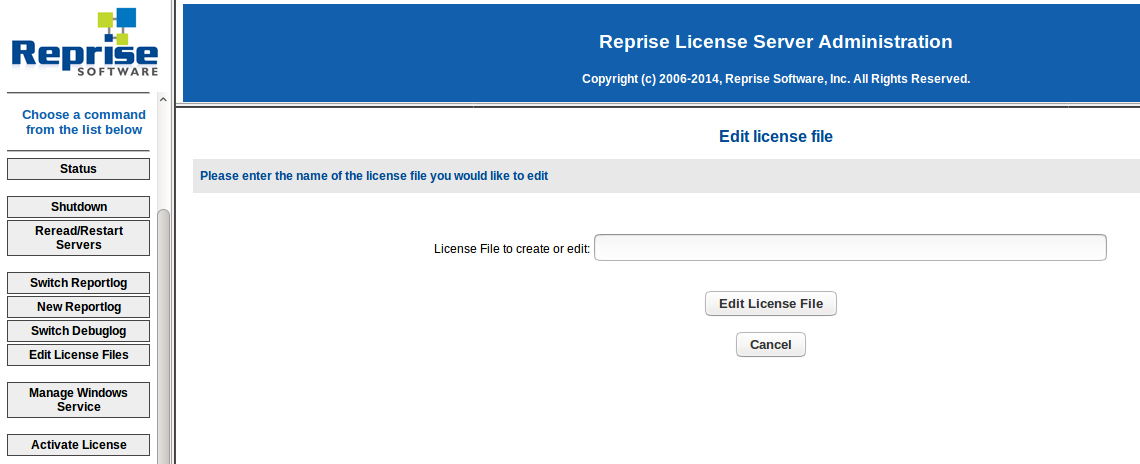
An attacker who can access the Web Management Interface can edit license files, license files have an arbitrary path where a person can edit. Changing the path to some other file will render it access to that file.
One interesting aspect is that you can write any extension for the file so .EXE files where an attacker could write executable files. However, the [<>&] aren’t allowed so introducing WebShells won’t be so easy.
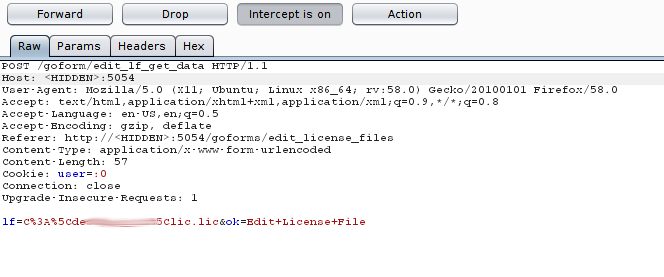
The vector itself that this vulnerability is refering will be located on the http(s)://ipOfServer:port//goform/edit_lf_get_data. Analyzing the request with burp we can see the parameter where a full path of a file is being send:
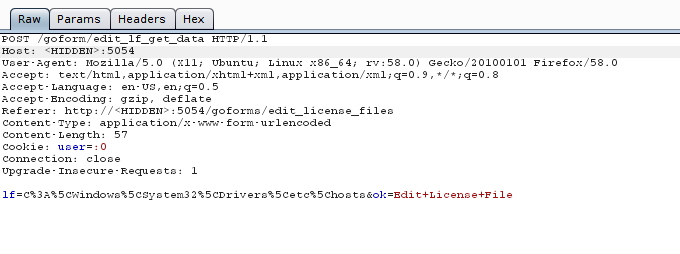
If we change the path to some file out of the directory structure, like for example the hosts file in windows we can see the response in the Web browser where the file will be presented:
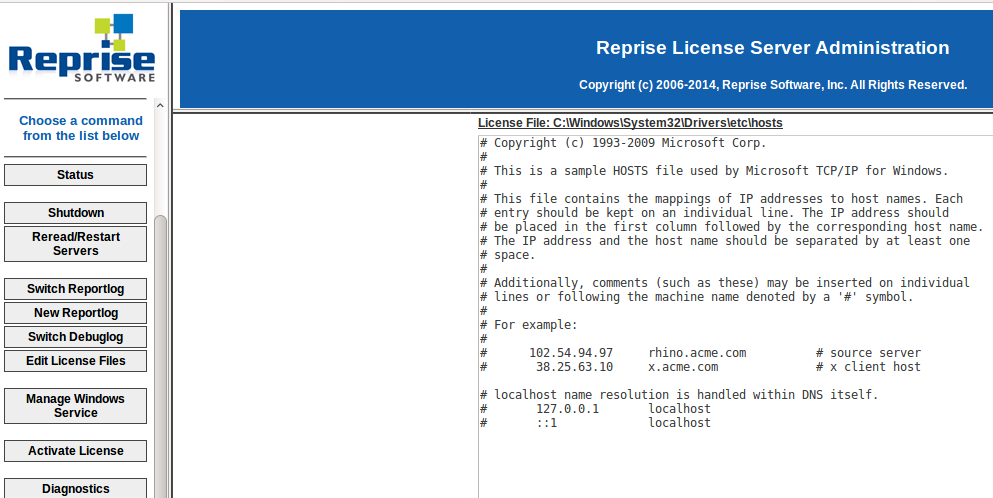
As we can see in the picture above a file outside the Web root was accessed without any control. The matter is worsen since the application accepts in the user interface any file, by direct input thus Reprise Software Inc. won’t consider this a vulnerability. However an attacker can overwrite some important files, like the application log hence hiding their tracks. A solution passes by limiting the file access to the directory structure or to a license folder, avoiding the writing of files with different extensions.
Next I present to you the form where you can input any file to be read (and then overwritten, giving the permissions):
For testing and record next is the about page where it states the product version:
On conclusion, this is my opinion only, that this behavior represents a danger since the attacker can read arbitrary data provided its stored on the disk AND we have permission to read. However a lot of information can be retrieved from files that have low permissions standards. The recommendation that the company gave me is to lower the permissions level so the application can’t read critical files, but I think that solution won’t be enough and based on the OWASP Path Transversal (OWASP Path Transversal) it is still considered a vulnerability. There is the possibility to disable the interface.
I hereby don’t incentive to exploit this vulnerability for malicious purposes and my research was only an academic one without interference or harm to any people.